Keeping Your Websites and APIs Secure
Edgio Web Application and API protection (WAAP) boosts security without sacrificing performance. Start protecting against evolving threats today.
Learn About Edgio’s Security Solutions

Why Edgio Security
Control, Secure, And Monitor Your Application
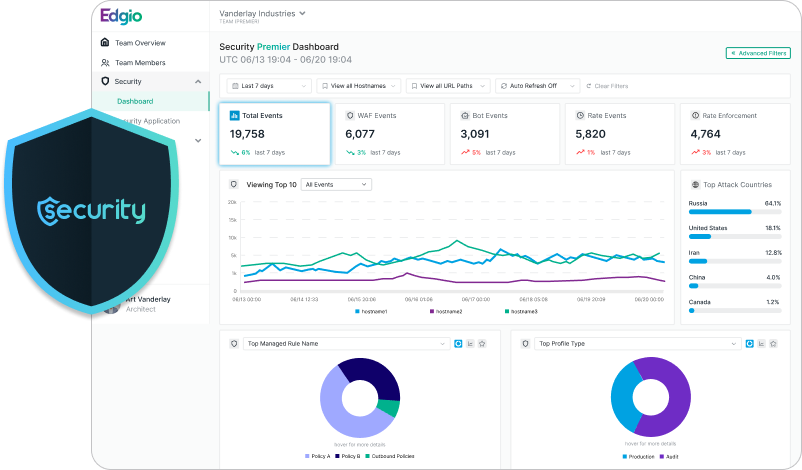
Modern edge security combined with Edgio’s unique dual WAAP configuration, provides true defense-in-depth against a wide range of threats targeting web applications and APIs. Edgio is proud to provide holistic Web Application and API Protection, delivered from the edge in one single console, simplifying security for all of our customers
Dual WAAP/WAF
Our unique Dual WAAP/WAF allows for faster threat containment with lower effort by your teams. Click here to learn more!
Managed Security Services
Our team brings proven expertise for comprehensive security and peace of mind. Click here to learn more!
Advanced Bot Protection
Our advanced bot management platform offers unparalleled defense against evolving bot threats. Click here to learn more!
DNS / DNSSEC
Safeguarding your domain from cyber threats by adding a layer of cryptographic security to DNS lookup processes.
DDoS Protection
Harness AI-driven DDoS protection to proactively identify and neutralize emerging cyber threats at the edge. Click here to learn more!
Origin Shield
Enhances content delivery speeds, providing a seamless user experience even during high traffic spikes.
What is it?
Boosts Security Without Sacrificing Performance
Leverage sophisticated security architecture with our multi-tiered Edge WAAP, incorporating seamless bot management, resilient DDoS mitigation, and extensive API protection capabilities, engineered for optimal performance.

Edgio provides holistic edge security to keep your business and your customers safe.
23%
Of all cybersecurity attacks hit finance and insurance organizations
70%
Of all attacks in the BFSI sector in 2022 were made on banks
$40,000
Can be lost from a
DDoS attack in just
one hour
Can be lost from a DDoS attack in just one hour
Simplified, Holistic Web Application Security
Disjointed solutions increase complexity and lead to security gaps. Choose a unified web application security platform that lowers risk.
- Single pane of glass reduces policy errors
- Deep observability and unified alert management with native web application and API protection
- Simple integration with existing DevSecOps and SOC tools


Advanced Bot Manager
Detect and mitigate evolving bot threats at the edge using signature fingerprinting, behavioral inputs, and patent-pending ML techniques
- Protects your business from automated threats including Account Takeover (ATO), Fake Account Creation, Scraping, Denial of Inventory, and more
- Categorized analytics via centralized reporting provide observability into both good and bad bots
- Supports multiple actions including alert (log only), block, browser challenge, CAPTCHA, custom responses, and redirects


Why Edgio Security
Distributed Denial of Service (DDoS) Protection
Edgio’s DDoS Protection automatically detects and mitigates massive, complex automated attacks before they affect your websites and applications.
- Software-defined, always-on protection backed by a 250+ Tbps global network
- Full spectrum DDoS protection from the network/transport layer to application layer
- Proprietary AI/ML algorithms and one of the largest Anycast networks on the globe route traffic efficiently, providing resilience for high traffic events and DDoS attacks

Detect and mitigate evolving bot threats at the edge using signature fingerprinting, behavioral inputs, and patent-pending ML techniques
- AI/ML discover all APIs in your ecosystem, including “shadow” and “zombie” APIs
- Apply a positive security model and only accept requests to that conform to your schemas
- Manage and secure internal, external and partner APIs

Faster Testing, Greater Confidence with Dual WAAP
Threats are increasing and constantly evolving. Dual WAAP mode enables teams to test new rules against production traffic in audit mode.
- Release virtual patches, faster, and with higher confidence
- Close the door on zero-day threats faster
- No more fire drills – dev team can stay focused on feature delivery











